Firewalling Zones with Interface Lists
The MikroTik Security Guide and Networking with MikroTik: MTCNA Study Guide by Tyler Hart are available in paperback and Kindle!
Preface
Mikrotik's RouterOS doesn't yet have specific functionality built in for network "Zones" like some other router platforms, but with new releases of RouterOS we can get the same functionality through "Interface Lists". An interface list is just like a firewall address list, except instead of host IPs or CIDR subnets we're listing physical or virtual interfaces. Once we've put interfaces into their respective lists we can use those lists in firewall rules. If you have many interfaces, such as multiple trunked VLANs or redundant WAN connections this could help you consolidate firewall rules.
Navigation
Zone Overview
I like to group my interfaces into zones based on the trust level of the network that an interface is attached to. Often we end up with "Trusted", "Semi-Trusted", and "Untrusted" zones, and some additional zones as needed depending on how a network is built. How you split up your zones will be dictated by your individual organization's security, compliance, legal, and operational requirements.
Zone Types
It's easy to think of three zone types - Trusted, Semi-Trusted, and Untrusted.
Trusted Zone
Interfaces in a Trusted zone would be internal wired LAN or VLAN gateway interfaces, and management interfaces. We have a reasonable level of trust that the hosts in these networks are not trying to actively compromise our systems, and so we allow them to communicate (relatively) freely. Access to these networks would require physically plugging into a port on-premise, and hopefully port security is in place adding an additional security layer.
Semi-Trusted Zone
A Semi-Trusted network could be a point-to-point VPN to a vendor's network, or a corporate wireless network. We must have these networks in place for legitimate business or organizational reasons, but there is a chance that a bad actor could get access to these networks and we want that breach to be contained if it occurs. Many organizations give these networks access to internal server resources (Active Directory DCs, DNS servers, etc) as required, but access to other subnets or services is forbidden.
Untrusted Zone
Untrusted networks are networks where we know or have reason to suspect that malicious activities could occur, or do occur. A good example of an Untrusted connection is a connection to the internet via an ISP. Port scans and malicious login attempts are very common out on the internet, and it's a given that attackers are actively searching for soft targets.
Guest wireless networks are great candidates for a custom zone with some additional firewall rules. It's still untrusted, because there's no telling what kind of devices might roam onto the network and what kind of issues they may bring with them. But even though the network is untrusted, it still has to forward traffic outbound to the ISP, and they may be allowed to resolve DNS names using an internal server if split DNS is configured, or they will just use a public DNS like Google's 8.8.8.8 server.
Creating MikroTik Zones
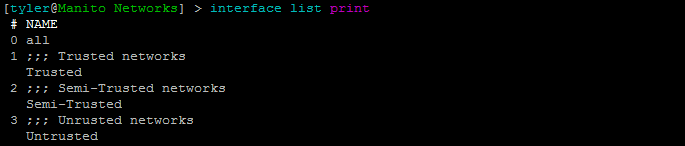
After you have decided what Zones to create and which interfaces should be in what Zone, the first step is to create empty Interface Lists:
/interface list add name="Trusted" comment="Trusted networks"
/interface list add name="Semi-Trusted" comment="Semi-Trusted networks"
/interface list add name="Untrusted" comment="Untrusted networks"
/interface list add name="Guest Wireless" comment="Guest Wireless"One Interface List already exists, number zero, the "all" list. It can't be deleted, but by default it isn't used anywhere either so it doesn't affect your security.
Now that we have lists we'll assign interfaces to the lists. In this case ether1 is our internet-facing WAN address, ether2-5 are LAN ports, wlan1 is a corporate (encrypted) wireless network, and wlan2 is an open (unencrypted) guest wireless network:
/interface list member add list=Semi-Trusted interface=wlan1 comment="Corporate WLAN"
/interface list member add list=Untrusted interface=ether1 comment="Pacific Telco WAN"
/interface list member add list="Guest Wireless" interface=wlan2 comment="Guest WLAN"
/interface list member add list=Trusted interface=ether2 comment="LAN"
/interface list member add list=Trusted interface=ether3 comment="LAN"
/interface list member add list=Trusted interface=ether4 comment="LAN"
/interface list member add list=Trusted interface=ether5 comment="LAN"With all of our interfaces in their respective lists we can use the lists in firewall rules. Having multiple interfaces in a rule means you only need to put the interface list in one rule, and that rule then applies to all those interfaces. For example, we can use an input-drop rule on all WAN interfaces by applying that rule to the "Untrusted" list:
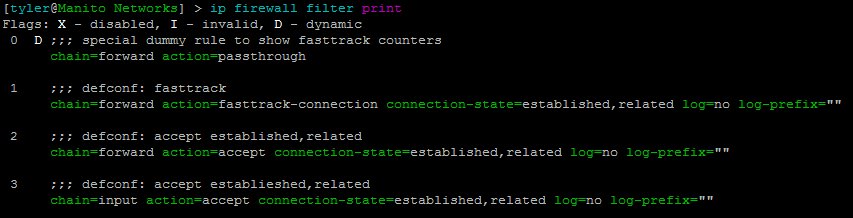
/ip firewall filter add chain=input in-interface-list=Untrusted action=drop comment="Drop input from WAN"We can allow all of our trusted networks on ether2-ether5 to forward traffic out the WAN to the internet by using just one rule:
/ip firewall filter add chain=forward in-interface-list=Trusted out-interface=ether1 action=accept comment="Trusted nets to internet"When new interfaces are added to the router all that needs to be done is adding the interface to the appropriate interface list, and the correct firewall rules will now apply. (adsbygoogle = window.adsbygoogle || []).push({});